- Part 1. How to mitigate APTs. Applied theory
- Part 2. Top-4 mitigation strategies which address 85% of threats
- Part 3. Strategies outside the Top-4. For real bulletproof defense
- Part 4. Forewarned is Forearmed: the Detection Strategy against Advanced Persistent Threats (APTs)
Part 1. How to mitigate APTs. Applied theory
It’s very likely that modern targeted attacks like operation Turla or El Machete are still active. Even if they aren’t, Kaspersky Lab’s GReAT (Global Research and Analysis Team) detects similar, significant espionage campaigns on a regular basis, all over the world.
Advanced Persistent Threats (APT) are complex attacks, consisting of many different components, including penetration tools (spear-phishing messages, exploits etc.), network propagation mechanisms, spyware, tools for concealment (root/boot kits) and other, often sophisticated techniques, all designed with one objective in mind: undetected access to sensitive information.
APTs target any sensitive data; you don’t have to be a government agency, major financial institution or energy company to become a victim. Even small retail organizations have sensitive client information on record; small banks operate remote service platforms for customers and businesses of all sizes process and hold payment information that is dangerous in the wrong hands. As far as attackers are concerned, size doesn’t matter: it’s all about the information. Even small companies are vulnerable to APTs – and need a strategy to mitigate them.
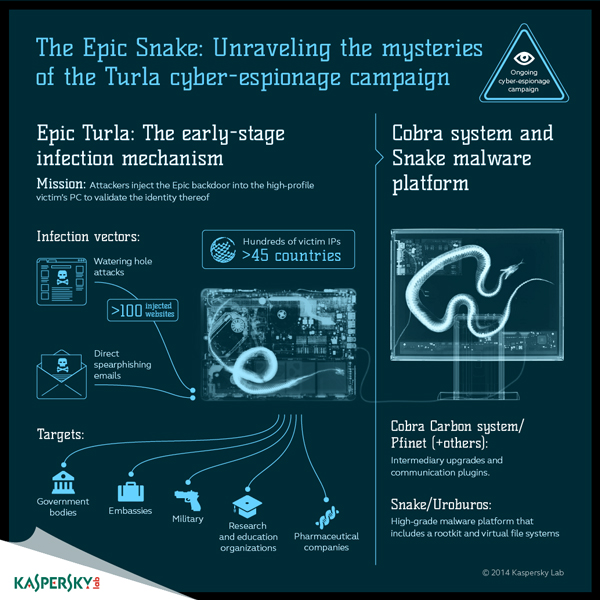
APTs have become a common occurrence. Epic Turla is an example of a highly effective, active campaign.
Counter-APT approaches: current theories
Many respected technology-focused organizations have already developed strategies for coping with targeted attacks. Gartner, for example, has issued guidelines for dealing with social engineering techniques, including keeping pace with an evolving threat landscape through ongoing information security education1.
Among the technical security issues addressed by Gartner, two key recommendations emerge: “Upgrade perimeter and network-based security” and “Focus protection strategies on malicious content”. In this context, Gartner mentions Kaspersky Lab among the leading vendors for Application Control and Whitelisting2, capable of providing all the functionality needed to mitigate against APTs.
The US Information Assurance Directorate (IAD) has also issued Information Assurance Mitigation Strategies with some reference to APTs. Here, the Directorate grouped measures into four key areas: device integrity, damage containment, account protection and secure and available transport. One of the most interesting practical guides to mitigating Targeted Cyber Intrusions comes from the Australian Signals Directorate. More about this below.
Effective mitigation strategies: some examples
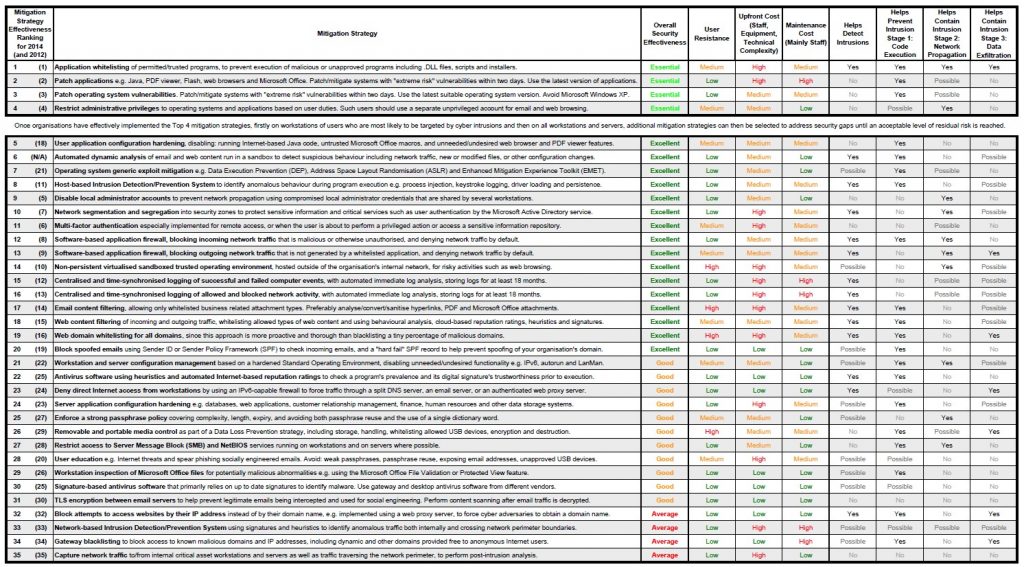
No ICT infrastructure can ever be 100% secure, but there are reasonable steps every organization can take to significantly reduce the risk of a cyber-intrusion . Through comprehensive, detailed analysis of local attacks and threats, Australia’s Signals Directorate (ASD) has found that at least 85 per cent of the targeted cyber intrusions it responds to could be mitigated by four basic strategies:
- Use application whitelisting to help prevent malicious software and unapproved programs from running
- Patch applications such as Java, PDF viewers, Flash, web browsers and Microsoft office
- Patch operating system vulnerabilities
- Restrict administrative privileges to operating systems and applications, based on user duties.3
These steps are considered so effective, they have been recommended for all Australian government agencies. Based on Kaspersky Lab’s deep counter-APT expertise and analysis, we believe that this approach would be effective not only for government agencies or large enterprises, but for smaller commercial organization as well.
No organization should assume its’ data is of little or no value. Attackers aren’t just looking for classified information – sensitive business details, intellectual property, scientific data and government policies are all being targeted. And even if they’re not interested in your sensitive data, criminals may well be interested in accessing your IT network, using it as a beachhead for an assault on a more attractive target.
At Kaspersky Lab, we strongly believe the Australian Signals Directorate top 35 mitigation strategies list is one of the most important publicly available guidelines to fighting targeted cyberthreats. We have carefully analysed it and correlated each point by technologies available in our products. Should you chose to apply ASD’s top 35 mitigation strategies list to your organization, Kaspersky Lab’s Products will make it not only easier but also more effective and safer.
The Australia’s Signals Directorate’s full Mitigation Strategies list comprises 35 points.
What exactly ASD’s Top ‘Mitigation Strategies’ offers
As shown above, the ASD’s Mitigation Strategies list consists of 35 points that could be roughly divided into four logical types, according to implementation approach:
| Measures | Brief description |
| Administrative | Training, physical security |
| Networking | These measures are easier to implement at a network hardware level |
| System administration | The OS contains everything needed for implementation |
| Specialized security solutions | Specialized security software is applicable |
The first measures are purely administrative: employee instruction and training, improving physical office security and so on. There is almost no mention of hardware or software other than measures to deploy systems for physical access control or online education.
At the network level, you can take many mitigating steps. For example, in tenth place on the list “Network segmentation and segregation” is classified as “excellent” for overall security effectiveness. In 23rd place – “Deny direct Internet access from workstations” is rated “good” (third grade after “essential” and “excellent”) in terms of importance for security.
After setting up your network hardware, you could do a lot just using operating system (OS) features. Strengthening systems against targeted attacks can create quite a lot of work for system administrators. To start with, the “essential” part one of four measures is restricting administrative privileges. Also turning on every possible built-in mechanism (ASLR and others) for software defense is strongly recommended. From a Kaspersky Lab perspective, the ‘specialized security solutions’ functionality is significant; this is an area in which Kaspersky’s software and technologies could help a lot, as you’ll see below.
The majority of mitigation strategy steps can be implemented using Kaspersky Lab’ security solutions.
- At least 85% of the intrusions the ASD responded to in 2011 involved adversaries using unsophisticated techniques that could have been mitigated using the top four mitigation strategies together: application whitelisting, updates /patching for applications, updates/patching for operating systems and minimizing administrative privileges . Kaspersky Lab products include technological solutions to cover the first three major Strategies; in addition, over half of the ASD list could be implemented using our specialized information security solutions. In the second part of this Strategies for Mitigating APTs series, we will explore this further.
| ASD’s rank | Mitigation strategy, short name | Kaspersky Lab technologies |
| 1 | Application whitelisting | Dynamic whitelisting |
| 2 | Patching application vulnerabilities | Vulnerability Assessment and Patch Management |
| 3 | Patching OS vulnerabilities | |
| 5 | User application configuration hardening | Web control (blocking scripts in web-browsers) , Web Anti-Virus |
| 6 | Automated dynamic analysis of email and web content | Mail Anti-Virus and Web Anti-Virus, Security for Mail Server, Security for Internet Gateway, DLP for Mail and Collaboration add-ons |
| 7 | OS generic exploit mitigation | Automatic Exploit Prevention |
| 8 | HIDS/HIPS | System Watcher and Application Privilege Control |
| 12 | Software-based application firewall for incoming traffic | Advanced Firewall |
| 13 | Software-based application firewall for outgoing traffic | Advanced Firewall |
| 15 | Computer event logging | Kaspersky Security Center |
| 16 | Network activity logging | Kaspersky Security Center |
| 17 | E-mail content filtering | Kaspersky Security for Mail Sever |
| 18 | Web content filtering | Web Control |
| 19 | Web domain whitelisting | Web Control |
| 20 | Block spoofed e-mails | Anti-Spam |
| 22 | AV software using heuristics and automated Internet-based reputation ratings | Anti-Malware |
| 26 | Removable and portable media control | Device Control |
| 29 | Workstation inspection of Microsoft Office files | Anti-Malware |
| 30 | Signature-based AV software | Anti-Malware |
ASD Strategies that can be implemented effectively using Kaspersky Lab’s product range.
1 Gartner: Best Practice for Mitigating Advanced Persistent Threats (document ID G00256438).
2 If necessary check terms in Technological Glossary.
3 Australian Signals Directorate, Strategies to Mitigate Targeted Cyber Intrusions