- Part 1. How to mitigate APTs. Applied theory
- Part 2. Top-4 mitigation strategies which address 85% of threats
- Part 3. Strategies outside the Top-4. For real bulletproof defense
- Part 4. Forewarned is Forearmed: the Detection Strategy against Advanced Persistent Threats (APTs)
Part 3. Strategies outside the Top-4. For real bulletproof defense
In Part 2 of this series, we looked at how the ‘Top 4’ APT mitigation strategies from ASD’s list can protect against 85 per cent of all threats. But what about the other 15 per cent? That’s where the other measures on the list come into play.
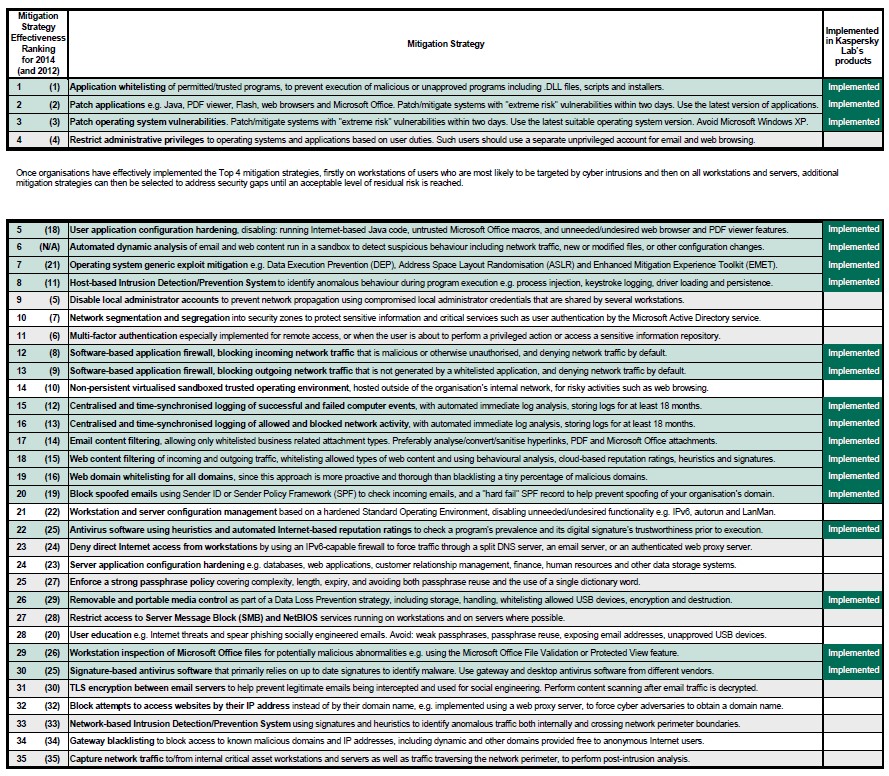
While there’s no such thing as 100 per cent security, Kaspersky’s recommended multi-layered approach to IT security delivers a highly effective defense against known and unknown threats. Kaspersky Lab’s technologies are capable of providing most of the 35 mitigation strategies recommended by the ASD1. Let’s take a look at them.
| ASD’s rank | Mitigation strategy, short name | Kaspersky Lab technologies |
| 1 | Application whitelisting | Dynamic whitelisting |
| 2 | Patching application vulnerabilities | Vulnerability Assessment and Patch Management |
| 3 | Patching OS vulnerabilities | |
| 5 | User application configuration hardening | Web control (blocking scripts in web-browsers) , Web Anti-Virus |
| 6 | Automated dynamic analysis of email and web content | Mail Anti-Virus and Web Anti-Virus, Security for Mail Server, Security for Internet Gateway, DLP for Mail and Collaboration add-ons |
| 7 | OS generic exploit mitigation | Automatic Exploit Prevention |
| 8 | HIDS/HIPS | System Watcher and Application Privilege Control |
| 12 | Software-based application firewall for incoming traffic | Advanced Firewall |
| 13 | Software-based application firewall for outgoing traffic | Advanced Firewall |
| 15 | Computer event logging | Kaspersky Security Center |
| 16 | Network activity logging | Kaspersky Security Center |
| 17 | E-mail content filtering | Kaspersky Security for Mail Sever |
| 18 | Web content filtering | Web Control |
| 19 | Web domain whitelisting | Web Control |
| 20 | Block spoofed e-mails | Anti-Spam |
| 22 | AV software using heuristics and automated Internet-based reputation ratings | Anti-Malware |
| 26 | Removable and portable media control | Device Control |
| 29 | Workstation inspection of Microsoft Office files | Anti-Malware |
| 30 | Signature-based AV software | Anti-Malware |
How Kaspersky Lab’s technologies map to the ASD’s Top-35 Mitigation Strategies for specialized security software.
User application configuration hardening, disabling running internet-based Java code, etc. – Ranked 5 with “Excellent” effectiveness
Among the main strategies outside the “big four” covered by Kaspersky Lab solutions, let’s take a look at User application hardening, including disabling Java code execution in the browser. Kaspersky’s Web Antivirus technology supports this technique through HTTP site content analysis. Site contents are scrutinized and, if necessary, blocked, based on security policies or threat presence. Administrators can set policies and rules to meet company-specific requirements. While Web Antivirus is capable of blocking unwanted/dangerous scripts from executing, Kaspersky’s Application Control prevents the use of unauthorized or unpatched browsers, PDF viewers and so on.
Because his specific approach is relevant for only the most popular browsers, all widely used software should also be setup correctly, with unneeded and insecure features turned off, according to the organization’s unique requirements and policies; it’s not appropriate for security solutions to automatically adjust legitimate applications or turn off features.
Automated dynamic analysis of email and web content – Ranked 6 with “Excellent” effectiveness
Automated, dynamic analysis of email and web content enables the detection of suspicious content and behavior – placing it at number 6 on the ASD’s list, with a rating of “Excellent” for effectiveness. Kaspersky Lab’s Mail and Web Anti-Malware capabilities, built around highly effective heuristic analysis, fit perfectly with this recommendation and are capable of detecting malware that can’t be found in traditional Anti-Virus databases.
Analyzers usually begin by scanning code for the kinds of suspicious content characteristic of malicious programs (static analysis). For example, many malicious programs search for executable programs, open the files found and modify them.
Despite high performance, static analysis detection rates for new malicious code are low, while the false positive rate is high. Kaspersky Lab’s technologies use a combination of static and dynamic analysis, emulating the execution of an application in a secure virtual environment. The dynamic method requires significantly more system resources than the static one, but offers much higher malware detection rates than the static method, with much lower false positive rates.
Automated dynamic analysis of email and web content should also be a part of every comprehensive specialized Anti-APT solution. Kaspersky Lab believes that, in addition to strong network traffic analysis, security systems should perform an analysis of attachments and other downloaded files in the sandbox.
Operating system generic exploit mitigation – Ranked 7 with “Excellent” effectiveness
Mitigation of generic exploits on operating systems can be partially implemented using native technologies (such as DEP, ASLR and EMET), but specialized security tools and technologies could raiseprotection to significantly higher levels.
Kaspersky Lab’s Automatic Exploit Prevention (AEP) significantly reduces the risk of targeted attack using exploits, even in the case of zero-day vulnerabilities. AEP mostly targets previously unknown exploits. Widespread malicious objects will be blocked by other security systems, such as Web Anti-Virus, File Anti-Virus or even the Anti-Spam filter, significantly enhancing the overall security of the end user.
Microsoft’s Enhanced Mitigation Experience Toolkit (EMET) may at first glance appear very similar to Kaspersky Lab Automatic Exploit Prevention (AEP). It is, however, a complementary rather than competitive technology, working in conjunction with Kaspersky Lab products to further strengthen defenses.
Microsoft’s technology blocks the execution of exploits using techniques including Data Execution Prevention (DEP) and Structured Execution Handling Overwrite Protection (SEHOP). EMET 5.0 also implements Attack Surface Reduction (ASR), preventing some plugins (including Java) from loading into Internet Explorer.
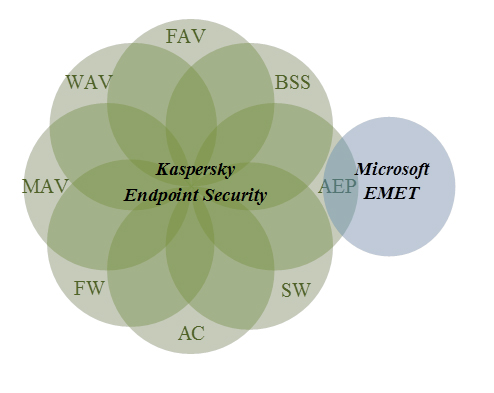
There is some overlap between Kaspersky AEP and EMET, but the differences between the two products far outweigh any similarities. In addition, AEP is just one component of the multi-layered defense strategy provided by Kaspersky Lab’s corporate and personal products. The full spectrum of technologies deployed in Kaspersky products, including Application Control (AC) and System Watcher (SW) among many others, is far broader in scope than what EMET is designed to provide.
The diagram below illustrates the interconnectivity between AEP and EMET, as well as the deep integration of SW and AEP into Kaspersky Lab’s products.
Whereas EMET is positioned solely as a mitigation tool, AEP is responsible for anomaly detection as well as threat mitigation. It works like this: System Watcher provides information on all of the main system events. This information on software behavior is compared with templates of typical malware functionality and behaviors. Based on this data, AEP discerns and detects suspicious application behavior. Kaspersky Lab’s technology provides ongoing situational analysis, comparing data from previous events, corresponding files, processes, reputations etc. to make decisions on whether to allow or block applications.
As for security mitigation, both AEP and EMET minimize the probability of vulnerability exploitation, placing many roadblocks in the way of exploits. This bilateral approach is a key advantage of AEP. It implements high-grade defense against exploits with minimal compatibility risks. Kaspersky Lab AEP is very easy to configure and works with previously installed software without any conflicts.
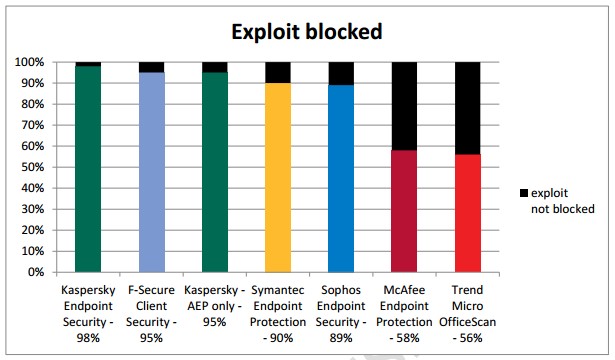
For consecutive years, Kaspersky Endpoint Security for Business has earned the best results in the Real World Enterprise Security Exploit Prevention Test carried out by MRG Effitas. The most recent tests took place between November 2013 and February 2014, following which Kaspersky Lab’s solution was awarded the MRG Effitas Certification.
Host-based Intrusion Detection/Prevention System – Ranked 8 with “Excellent” effectiveness
Kaspersky’s System Watcher and Application Privilege Control functionality between them deliver effective Host-based Intrusion Detection/Prevention Systems (HIDS/HIPS).
System Watcher collects data about the actions performed by applications on endpoints and gives this information to other components to help improve protection. System Watcher makes security decisions using data from regularly updated databases on patterns of dangerous application behavior. Upon detection of a new virus or modification to already known malware, our experts add a new pattern to the heuristics database, updating it together with Kaspersky Lab’s antivirus databases. This technology allows you to block other malicious software with similar behavior and roll back actions performed by malicious applications.
Along with registry modifications and process injections System Watcher also stops keylogging activity. Some signs of keylogging are mentioned in templates for malicious behavior detection.
Application firewall, blocking incoming/outgoing traffic – Ranked 12 and 13 with “Excellent” effectiveness
Following a simple modification to Kaspersky’s out-of-box firewall settings, ASD’s 12th and 13th strategies for software-based application firewalls can be implemented.
Firewalls apply rules to all network connections, either blocking or allowing any detected connection attempt. Protection against various types of attack is performed on two levels: network and application.
Blocking unnecessary network connections reduces the potential attack surface by limiting exposure to network services. Blocking outgoing network traffic that is not generated by trusted applications helps prevent cyber adversaries from exfiltrating organizational data, meaning complicated multilayered attacks have fewer chances to succeed.
The firewall protects personal data stored on a local host by blocking all threats that can be potentially dangerous for the operating system while the host is connected to the Internet or LAN. It filters all network activity using two types of rules: software network rules and network package rules.
Logging of computer events/network activity – Ranked 15 and 16 with “Excellent” effectiveness
Kaspersky Security Center logs both computer events and network activity. Event logs can be viewed in the standard Microsoft Windows Management Console and can also be exported in .evtx format. Such centralized logging is crucial for effective system administration.
Logs are, nevertheless, much more useful when used in conjunction with tools for interpretation and easy report generation by security officers. That’s why Kaspersky Lab’s solution has added support for leading Security Information and Events Management (SIEM) systems, such as ArcSight and Qradar2. At this stage, most security-critical events will be transmitted, such as warnings about unwanted content, blocking file access, detections of different types of malware and so on.
E-mail content filtering – Ranked 17 with “Excellent” effectiveness
Kaspersky Security for Mail Sever scans incoming, outgoing and stored e-mail, protecting the latest versions of major mail and collaboration platforms, including Microsoft Exchange, IBM Lotus Domino, and Linux-based mail servers. Intelligent, cloud-assisted spam filtering for Microsoft Exchange and Linux-based mail servers works in real-time to significantly reduce the traffic load caused by unwanted messages.
Application whitelisting protects endpoints as part of Kaspersky Endpoint Security. It controls the execution of downloaded files and mail attachments. Kaspersky Endpoint Security also analyzes PDF and Microsoft Word files using reputation databases.
Web content filtering – Ranked 18 with “Excellent” effectiveness
Kaspersky’s Web Anti-Virus enables web-traffic filtering, protecting systems from malicious software delivered via HTTP and HTTPS protocols. This component also scans FTP traffic. Kaspersky Anti-Virus for Proxy Server filters web traffic using both heuristics and signatures, cloud-based reputational ratings. Web Control categorizes content before allowing or denying, depending on its nature.
Each open web page or file intercepted by Web Anti-Virus is analyzed for malicious code and anomalies. If a web page or other object is considered dangerous, access will be blocked. If the web page or the object is not infected, it’s allowed to load as usual. This mitigates so-called ‘Waterhole’ attacks, where criminals infect popular legitimate web sites (news, etc.) in an attempt to access the systems of regular users. Sites with technical information, useful for system administrators, are popular targets for criminals hoping to infect PCs with access to administrative rights and other critical information.
Spearphishing and waterholing are the most popular ways of launching targeted attacks, but they’re not the only ones. Kaspersky Lab’s technologies prevent malicious activities from being launched via web site, regardless of the malefactor’s method of attack. It could be social engineering, a link form search results, etc.
Domain whitelisting for all domains – Ranked 19 with “Excellent” effectiveness
Kaspersky Lab’s Web Controls enable system administrators to develop and maintain white lists of domains for their organization. Web Control filters HTTP/HTTPS traffic according to the organization’s internal policy – usually the blocking of social networks, music, video and non-corporate web e-mail during business hours.
Web Control operates similarly to firewalls. The administrator creates a set of block/allow rules. The rule properties include user accounts, schedule, content and output. The rules are applied in the order specified by the administrator and a page is processed according to the first applicable rule.
Using heuristics and automated Internet-based reputation ratings – Ranked 22 with “Good” effectiveness
Advanced Anti-malware, the core of all Kaspersky Lab products, uses heuristics and automated Internet-based reputation ratings – essential components of effective IT security. Files and URL reputations are available through Kaspersky Security Network.
Portable media control – Ranked 26 with “Good” effectiveness
Kaspersky’s Device Control technology helps maintain and secure removable and portable media. It enables administrators to monitor various devices on the corporate network and, if necessary, prohibit using some of them. The most popular use case for this component is blocking unauthorized USB flash drives.
Workstation inspection of Microsoft Word files – Ranked 29 with “Good” effectiveness
Microsoft Word documents are just one of the file types Kaspersky Lab Advanced Anti-Malware core analyzes. This control is a useful addition to built-in Microsoft Office Protected View and security add-on Office File Validation.
Signature-based Anti-malware software – Ranked 30 with “Good” effectiveness
Kaspersky Lab’s Advanced Anti-malware core uses a traditional file signatures base, among other detection methods. Kaspersky Lab’s products interoperate well with other vendor’s software on different device types, as per ASD strategy recommendations. For customers seeking to follow every letter of this mitigation strategy and choosing different vendors for endpoints and gateways, we recommend using Kaspersky Lab’s products on the endpoints – our success in multiple independent tests speaks for itself.
The multi-layered combination of File and Web Anti-malware, Web, Device and Application Control, Advanced Anti-phishing and other technologies, all managed via a single console in the Kaspersky Security Center, enables effective protection against targeted attacks. Each of the technologies mentioned in this series forms part of Kaspersky Endpoint Security for Business. Kaspersky Security for Mail Server is available in the Total tier only; for all other technologies, Advanced tier is quite sufficient.
Kaspersky Lab Technological Leadership: More than just another security vendor.
Kaspersky Lab is more than just another security vendor promising to protect your IT infrastructure from almost any threat. Information security is in our DNA: our technologies are built on Kaspersky Lab’s global intelligence network, with more than 60 million Kaspersky Security Network volunteers worldwide. This security cloud processes over 600,000 requests every second.
Our elite group of security experts – Global Research and Analysis Team – is an integral part of Kaspersky Lab’s strategy. Their main focus is the discovery and analysis of new cyber weapons, along with the prediction of new types of threats; Kaspersky Lab’s reputation for discovering and mitigating against the most relevant, sophisticated threats, such as Epic Turla, Careto and Red October are the result of this dedication and commitment to research and development.
Kaspersky Lab’s expertise is recognized and respected among top security organizations globally. It is our principled position to detect and remediate any attack, regardless of its origin or purpose. We cooperate and consult with Interpol, Europol and many national CERTs.
A purely technology driven company, more than one third of Kaspersky Lab’s employees work in research and development. All our solutions are developed in-house on a single code base. Our leadership and expertise is proven in multiple independent tests. In calendar year 2013 we participated in 79 tests and reviews. 61 times Kaspersky Lab was named in the “top-3” and 41 times was rated first place.
All of these things combine to give Kaspersky Lab a deep understanding of IT security risk mitigation, making Kaspersky Lab’s solutions among the best available to implement your company’s mitigation and threat management strategies.
1 See Parts 1 and 2 of this series for further details of the Australian Signals Directorate’s Threat Mitigation Strategy
2 Included in Kaspersky Security for Business 10 SP1; release scheduled for spring, 2015