Phishing is a type of Internet fraud that seeks to acquire a user’s credentials by deception. It includes theft of passwords, credit card numbers, bank account details and other confidential information.
Phishing messages usually take the form of fake notifications from banks, providers, e-pay systems and other organizations. The notification will try to encourage a recipient, for one reason or another, to urgently enter/update their personal data. Such excuses usually relate to loss of data, system breakdown, etc.
Phishing attacks are becoming more advanced in their exploitation of social engineering techniques. In most cases, fraudsters try to frighten a recipient by providing a seemingly important reason that the recipient should divulge their personal data. Such messages usually contain threats to block an account if a recipient does not fulfill the requirements therein. For instance, “if you do not provide your personal data by the end of the week, your account will be blocked”. Ironically, it is not unknown for phishers to make reference to the necessity of improving anti-phishing systems as one of the reasons for the disclosure of confidential information. A typical ruse might be “if you want to secure yourself against phishing, click the link and enter your user name and password”.

Pic. 1. A sample of a phishing message, purportedly from the National Credit Union Administration,
containing a request to click the link and update the user’s data.
The average lifetime of a phishing site is 5 days. Anti-phishing filters receive information about a new threat very quickly and so phishers constantly have to register new sites that imitate the official sites of various different credible organizations.
In order to access a fake site the user has to enter their credentials. This information is exactly what the phishers are after. Once they get access to a user’s email box or bank account, the phishers then face the problem of removing cash from that victim’s account without leaving a trail, and that is not an easy thing to do. If a person involved in this illegal business gets caught by law enforcement authorities, they will surely be prosecuted. This is why phishers sell the stolen data to other fraudsters who already have proven schemes for the withdrawal of money from bank accounts in place.
Banks, e-pay systems and e-auctions are major targets for phishers. This indicates that fraudsters are most interested in personal data which provides access to money. The theft of email credentials is also popular however, because this information can be sold to those who distribute viruses or create zombie networks.
The ‘quality’ of phishing messages is usually very high. A fake site will generally look exactly like the original so that a user will not suspect anything is wrong when they enter their user name and password to access the site.
Another phishing trick is to use links that look similar to the URLs of credible sites. This trick is designed to ensnare less experienced users. A careful user will notice that a link in the browser command line is in fact different from that of the legitimate site. These links may begin with an IP address, though big companies do not commonly use links such as these any more.
As such, phishing URLs often closely resemble the genuine URL of a legitimate company. They may include the name of the original URL with some additional words (for example www.login-examplebank.com instead of www.examplebank.com). Another trick is to use dots instead of slashes (for example www.examplebank.com.personal.login or www.examplebank.com-personal.login instead of www.examplebank.com/personal/login).
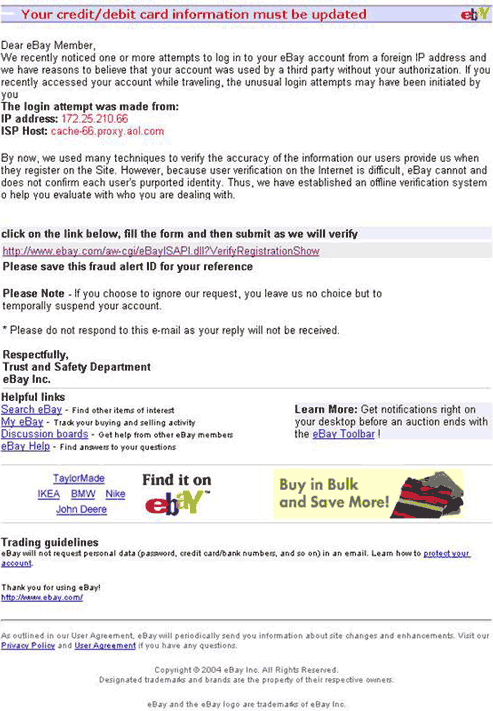
Pic.2 A sample of a phishing message (imitation of an EBay notification)
containing several links with one of them leading to a phishing site.
The body of a message seemingly contains a link to a legitimate site, but the URL may be different. A user’s vigilance may be dimmed by a few additional links to the official site, but the main link, which requires the user to enter their name and password, leads to the fake site.
Sometimes a user is required to enter their confidential data on the same page as the message itself. Everyone should be alert to the fact that no legitimate bank or other similar organization would ever ask a user to do this.
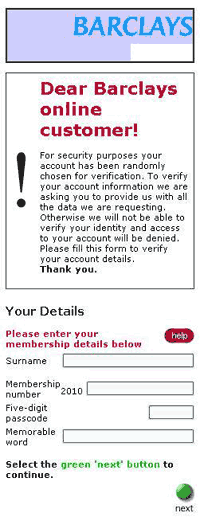
Pic.3. A phishing message imitating a notification from Barclays Bank
asking the user to enter their login credentials on the same page as the message.
Phishers are constantly improving their technologies and this has resulted in the appearance of a new trend – ‘Pharming’. This type of Internet fraud also targets access credentials such as user names and passwords, but unlike phishers who use email to achieve their goals, pharmers obtain identities via official websites. They redirect users to bogus websites by changing legitimate digital website addresses on DNS servers to fake ones. Pharming is an even more serious threat because it is next to impossible for the user to spot the fact that they are being scammed.
The most popular phishing targets are Ebay and PayPal. Other targets include banks all over the world. Phishing attacks can be random or targeted. Random attacks are aimed at the most popular sites such as Ebay because there is a strong possibility that a recipient will have an account there. In the second case, fraudsters determine beforehand that the user has an account with a certain bank, e-pay system, provider etc. This method is more complicated and costly for the phishers, but the corresponding likelihood that a victim will be hooked is also higher.
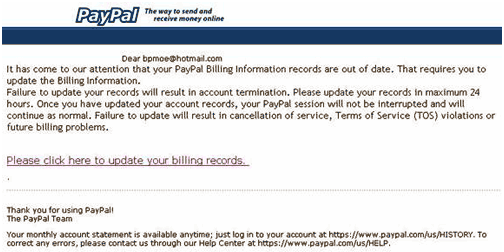
Pic.4 A sample of a phishing message imitating a notification from the popular PayPal e-pay system.
Identity information theft is not the only threat presented by a phishing link. It may lead to spyware, a keylogger or a Trojan program. So even if a user does not have an account which can be targeted by fraudsters, they are never completely safe.
According to Gartner, in 2006, the average US phishing victim lost $1244, whilst in 2005 the figure did not exceed $257. These figures prove the phishers’ incredible success. However in Russia the situation is different. Systems that use e-pay are not as popular as they are in the West, thus the damage caused by phishing is not so great. When e-pay systems become more widespread in Russia the share of phishing emails compared to the total volume of email traffic will increase and this will result in correspondingly higher levels of fraud. This problem is not significant in Russia at present, but it is necessary to start preparing for it today.
The success of phishing is largely determined by the low levels of user-awareness regarding how the companies which fraudsters try to imitate, operate. Many legitimate sites contain special warnings saying that they never ask users to send confidential data in messages. However, users continue to send their passwords to phishers. That is why a few years ago an Anti-Phishing Working Group (APWG) was established which included both the companies that the phishers target, and anti-phishing/antispam software vendors. APWG holds information sessions to try to inform users about the problem. In addition APWG members inform each other about new phishing sites and threats. Currently APWG includes 2500 members. Big international banks and leading IT companies are among them. According to optimistic forecasts, in the near future, users will learn to be as wary of phishing sites as they have become of messages with attachments from unknown senders. Meanwhile spam filters remain the first line of defense against phishing.
Related products and services
Kaspersky Premium for home
Kaspersky NEXT for business
Kaspersky Security for mail servers