Note: these rules only apply to Malware and do not concern Adware, Riskware, Pornware, or other objects detected using proactive defense (which take the PDM: prefix) or the heuristic analyzer (which take the HEUR: prefix).
According to the standard classification system, each detected object has a clear description and an unambigous place in the classification tree.
However, in real life there are malicious programs which have a wide range of malicious functions and propagation routines. Let’s use a malicious program that spread by email as an attachment and via P2P networks as files as an example. This malicious program also has the ability to harvest email addresses from an infected computer without the consent of the user. As a result, the malicious program (according to the classification system) could be correctly classified as Email-Worm, P2P-Worm, or Trojan-Mailfinder. Ultimately, different modifications of the same malicious program can be classified differently depending on which behaviour seems most outstanding to the malware analyst who analyzed the code. This only causes confusion.
In order to avoid this problem, Kaspersky Lab uses a set of rules which help to unambiguously categorize a malicious program as having a particular behaviour, regardless of the program functions.
How do the rules work? Each behaviour is assigned its own threat level: the behaviours which post less of a threat are outranked by behaviours which post more of a threat. In the example above, the most threatening behaviour is Email-Worm, and the malicious program should therefore be classified as such.
The rules for all types of malware can be shown in the form of a tree:
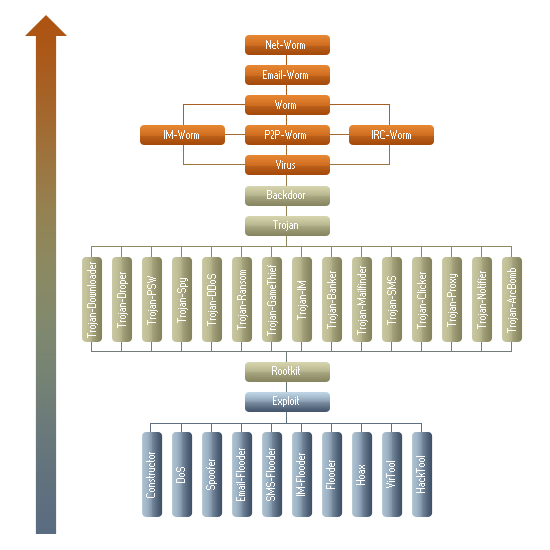
The rules for classifying detected objects with multiple functions
The types of behaviour which pose the least threat are represented in the lower part of the figure above, while the types of behaviour which pose a great threat are found in the upper part.
If a program can be categorized as a number of different behaviours, it should be classified as the most threatening of those behaviours. If a malicious program is covered by more than one type of behaviour (such as Trojan-Downloader and Trojan-Dropper, for example), then the behaviour higher up the tree takes precedence over the other behaviour.
Note: the rule for choosing the highest-ranking behaviour only applies to Trojans, Viruses and Worms. It does not apply to Malicious Tools.
If a malicious program has two or more functions with equal threat levels, which could be covered by Trojan Ransom, Trojan ArcBomb, Trojan Clicker, Trojan DDoS, Trojan Downloader, Trojan Dropper, Trojan IM, Trojan Notifier, Trojan Proxy, Trojan SMS, Trojan Spy, Trojan Mailfinder, Trojan GameThief, Trojan PSW or Trojan Banker, then the program will be classified as a Trojan.
If a malicious program has two or more functions with equal threat levels, which could be covered by IM-Worm, P2P-Worm, or IRC-Worm, that program will be classified as a Worm.