The aim of all virus writers and cybercriminals is to disseminate their virus, worm or Trojan across as many computers or mobile telephones as possible. This can be achieved through one of two ways:
- by social engineering
- by infecting a system without the user’s knowledge
These methods are often used simultaneously and usually include processes to circumvent antivirus programs as much as possible.
Social engineering
Social engineering techniques lure an unwary user into launching an infected file or opening a link to an infected site by underhand means. This method is employed by numerous email worms and other types of malware.
The task of hackers and virus writers is to attract a user’s attention to a link or to the infected file itself and make the user click on it. A classic example of the genre being the LoveLetter worm which created a real storm back in May 2000, and according to Computer Economics, still remains the most devastating in terms of the financial damage that it inflicted. Below is the message that the worm displayed on the screen:
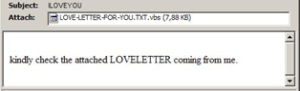
The ‘I LOVE YOU’ message was opened by an enormous amount of people, and that led to many a company’s email server going into meltdown as the worm copied itself to all of the contacts in a user’s address book once the attached VBS file was opened.
The Mydoom email worm which appeared on the Internet in January 2004 used texts that imitated the technical messages issued by the mail server.
The Swen worm passed itself off as a message from Microsoft and masqueraded as a patch to remove Windows vulnerabilities. Little wonder that people took it seriously and tried to install the ‘patch’.
Sometimes exceptional things happen. One such event dates back to November 2005. A version of the Sober worm informed users that the German police were investigating people who had visited illegal websites. This message was read by a man who used to frequent child pornography sites. He believed the message to be genuine and turned himself in to the police of his own volition.
Links to infected sites and files hidden inside emails have become very popular of late, with potential victims receiving messages sent via email, ICQ and other IM systems, or occasionally via IRC Internet chatrooms. Mobile viruses are delivered by SMS message. A message usually contains an attractive text which encourages the unsuspecting user to click on the link. This method of system penetration is the most popular and effective because it allows the malware to bypass the mail server’s antivirus filters.
P2P networks are also quite often used. A worm or a Trojan appears on the P2P network using a name designed to attract attention, for example:
- AIM & AOL Password Hacker.exe
- Microsoft CD Key Generator.exe
- PornStar3D.exe
- play station emulator crack.exe
When searching for programs, P2P users see these names, download the files and launch them.
Another trick is to offer the victim a free utility or a guide to accessing e-pay systems. For example, a user is offered the possibility of gaining free Internet/cellular access, or the chance to download a credit card number generator, or to increase their own online account balance, etc. A victim of such a scam cannot exactly complain to the police that their own illegal intentions were sidelined because they themselves became the victims. Cybercriminals are aware of this and take advantage of this situation a great deal.
An unknown Russian fraudster tried something unusual back in 2005-2006. A Trojan was sent to some addresses taken from the job.ru site, which specialized in recruitment. Some people who placed their CVs on this site received ‘job offers’ that included the Trojan. Interestingly, the attack mainly targeted corporate email addresses. It is most likely that the cybercriminals knew that the staff who received the Trojan would not want to tell their employers that they picked it up whilst surfing for alternative employment, and they were right – it took Kaspersky Lab’s specialists more than half a year to discover how this Trojan penetrated users’ computers.
There were a few exotic cases whereby a user received a fake email from their bank asking them to confirm their access codes, thus unwittingly revealing them to the scammer. The procedure that the user had to follow was so convoluted as to be ridiculous – print out the document, fill in the form and then fax it to the indicated telephone number.
Another unusual case happened in Japan in the autumn of 2005 when cybercriminals used a home-delivery service to distribute CDs infected with Trojan spyware. The disks were delivered to the clients of a Japanese bank, whose addresses had been stolen from the bank’s database.
Implementation techniques
Cybercriminals can use techniques that covertly introduce malicious code into a system by exploiting vulnerabilities in the security functions of the operating system and in the software. Vulnerabilities allow a networm or Trojan to penetrate a victim’s machine and launch itself.
Vulnerability is in fact a mistake in the code or logic of operation of the various programs. Current operating systems and applications are complex in structure and have extensive functionality, which makes it almost impossible to avoid mistakes in their design. This fact is actively used by virus writers and cybercriminals.
The Nimda and Aliz mail worms exploited Outlook’s vulnerabilities. In order to launch the worm file it was enough to open an infected message, or simply put the cursor on it in the preview window.
Malicious programs also actively exploit vulnerabilities in OS network components. This technique was used by CodeRed, Sasser, Slammer, Lovesan (Blaster) and other worms working under the Windows OS. Linux was affected too – with the Ramen and Slapper worms penetrating computers via vulnerabilities in this operating system and its applications.
Implementation of malicious code via web pages has recently become one of the most popular infection techniques. This technique exploits the vulnerabilities in Internet browsers. An infected file and a script program which exploit the browser’s vulnerability is placed on a web page. When a user enters an infected page the script program downloads the infected file to the user’s computer via the vulnerability and launches it. In order to infect as many machines as possible it is necessary to tempt large numbers of users to visit the web page. This can be achieved by different means, for example by sending out spam messages containing the address of the infected page, or by sending the same messages via IM systems (sometimes fraudsters even use search engines for these purposes). The text placed on an infected page is processed by search engines and the link to this page is then included in the list of other pages in search results.
Smaller Trojans designed to download and launch larger Trojans is another type of specialized malware. They enter a user’s computer by some means or other, for example via a system vulnerability, and then they download and install other malicious components from the Internet. Such Trojans often change the browser’s settings to their least secure in order to pave the way for the other Trojans.
Once discovered, vulnerabilities are quickly patched by vendors. However, they are immediately replaced by new vulnerabilities which hackers and virus writers start exploiting almost at once. In order to increase their own numbers, many Trojan ‘bots’ utilize new vulnerabilities whenever they arise, and weaknesses in Microsoft Office are often used to introduce Trojans too. Unfortunately the period between the appearance of the latest vulnerability and the start of its exploitation by worms and Trojans tends to become shorter and shorter. As a result, the vendors of the vulnerable software and the antivirus vendors frequently find themselves battling against time. The original vendor must rectify their mistake as soon as possible, test the result (usually called ‘patch’) and distribute it to the users. The antivirus vendors must immediately release a solution that detects and blocks the files, network packets or whatever that exploit the vulnerability.
Simultaneous use of implementation techniques and social engineering methods
Cybercriminals often use both methods simultaneously: social engineering – to attract the attention of a potential victim and technical means – to increase the possibility of an infected object penetrating a system.
For example, the Mimail mail worm was distributed as an email attachment. The email contained specially arranged text designed to make it noticeable to the user, and in order to launch a worm copy from the attached ZIP archive, virus writers used a vulnerability in Internet Explorer. When opening the file from the archive, the worm created a copy of itself on the disk and launched itself without any system warnings or additional user input. Incidentally, this worm was one of the first designed to steal personal data from users’ online accounts.
Another example is spam with a header saying ‘Hello’ and containing the text ‘Look what they say about you’. The text was followed by a link to a website. Analysis showed that the website contained a script which downloaded LdPinch, a Trojan designed to steal passwords from a user’s computer by exploiting a vulnerability in Internet Explorer.
Combating antivirus programs
The aim of cybercriminals is to introduce malicious code to a victim’s machine. To achieve their goal they must either force a user to launch an infected file or penetrate the system through a vulnerability that evades any antivirus filtering. It is hardly surprising that fraudsters try to actively combat antivirus programs. They use different techniques to do this, but most common are the following:
- Code packing and encrypting. The majority of current worms and Trojans are packed and encrypted. What’s more, black-hat programmers design special utilities that are used for packing and encrypting. For example, every Internet files processed using CryptExe, Exeref, PolyCrypt and some other utilities, have turned out to be malicious.In order to detect such worms and Trojans, antivirus programs must add either new unpacking and decoding methods, or signatures for each sample of a malicious program. This inevitably leads to a decrease in detection rates as no antivirus company can possibly have samples of every piece of malware at its disposal.
- Code mutation is mixing the Trojan’s code with ‘spam’ instructions, resulting in the change of its appearance, whilst retaining the Trojan’s functionality. Sometimes mutation happens in real-time, i.e. every time that a Trojan is downloaded from an infected website. It means that all, or almost all, Trojans that are downloaded to users’ computers are different. The Warezov mail worm, which caused some serious epidemics in the second half of 2006, is an illustration of this technique.
- Stealth techniques. The so-called rootkit technologies generally employed by Trojans are used to intercept and substitute system functions which make the infected file invisible to the operating system and antivirus programs. Sometimes even the registry branches where the Trojan is registered, along with other system files, are hidden. These techniques are actively used by the HacDef backdoor Trojan, for example.
- Blocking antivirus programs and antivirus database update systems. Many Trojans and network worms take special actions directed against antivirus programs – they search for them in the list of active applications and try to block them, damage their antivirus databases and block their update processes, etc. Antivirus programs have to defend themselves adequately by controlling the integrity of their databases and by hiding their processes from Trojans, etc.
- Masking of the code on a website. The webpage addresses that contain Trojan files soon become known to antivirus companies, i.e. virus analysts study the content of these pages and add new versions of Trojans to their databases. In order to combat antivirus scanning, a webpage can be modified, thus if the request was sent by an antivirus company, a non-Trojan file is downloaded instead of a Trojan.
- A ‘Quantity’ attack is the generation and distribution of large quantities of new Trojan versions across the Internet within a short period of time. As a result, antivirus companies receive huge amounts of new samples and it takes time and effort to analyze each one, which gives the malicious code an additional chance to successfully penetrate users’ computers.
These techniques are used by cybercriminals to combat antivirus programs. The fraudsters’ activity is growing every year and now it’s possible to speak of a ‘technological arms race’ between the antivirus and the virus industries. At the same time the number of individual hackers and criminal groups is also growing, as well as their professionalism. All of these factors considerably increase the complexity and the volume of work that antivirus companies have to do in order to develop suitably robust solutions.