A distributed network of ‘honeypots’, computers running special network traffic capture software, can be used to easily track the distribution of the most popular exploits and commonly exploited vulnerabilities. Collecting data from a reasonably large number of systems,and sorting it by type, source and destination provides statistics on the most common attacks, the most secure (or insecure) geographical areas and how the preferences for one set of exploits or another changes over time.
For instance, here’s the list of the most exploited vulnerabilities collected by the Smallpot project for September 2004:
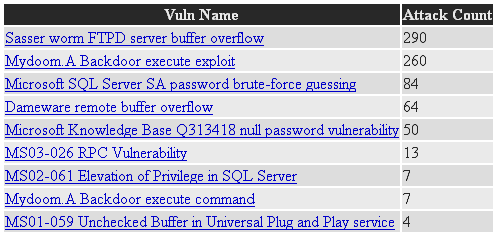
Most exploited vulnerabilities reported by the Smallpot project in September 2004
The SANS (SysAdmin, Audit, Network, Security) Institute and the National Infrastructure Protection Center (NIPC) at the FBI also releases a document listing the most critical Internet security vulnerabilities every year.
This is SANS Top 20 vulnerabilities for 2004:
- Top Vulnerabilities to Windows Systems
- W1 Web Servers & Services
- W2 Workstation Service
- W3 Windows Remote Access Services
- W4 Microsoft SQL Server (MSSQL)
- W5 Windows Authentication
- W6 Web Browsers
- W7 File-Sharing Applications
- W8 LSAS Exposures
- W9 Mail Client
- W10 Instant Messaging
- Top Vulnerabilities to UNIX Systems
- U1 BIND Domain Name System
- U2 Web Server
- U3 Authentication
- U4 Version Control Systems
- U5 Mail Transport Service
- U6 Simple Network Management Protocol (SNMP)
- U7 Open Secure Sockets Layer (SSL)
- U8 Misconfiguration of Enterprise Services NIS/NFS
- U9 Databases
- U10 Kernel